Custom patterns are user-defined patterns that you can use to identify secrets that are not detected by the default patterns supported by secret scanning. For more information, see Defining custom patterns for secret scanning.
At the enterprise level, only the creator of a custom pattern can edit the pattern, and use it in a dry run. There are no similar restrictions for editing custom patterns at repository and organization level.
Editing a custom pattern
When you save a change to a custom pattern, this closes all the secret scanning alerts that were created using the previous version of the pattern.
-
Navigate to where the custom pattern was created. A custom pattern can be created in a repository, organization, or enterprise account.
- For a repository or organization, display the "Security & analysis" settings for the repository or organization where the custom pattern was created. For more information, see Defining a custom pattern for a repository or Defining a custom pattern for an organization.
- For an enterprise, under "Policies" display the "Advanced Security" area, and then click Security features. For more information, see Defining a custom pattern for an enterprise account.
-
Under "Secret scanning", to the right of the custom pattern you want to edit, click .
-
When you're ready to test your edited custom pattern, to identify matches without creating alerts, click Save and dry run.
-
When you have reviewed and tested your changes, click Publish changes.
-
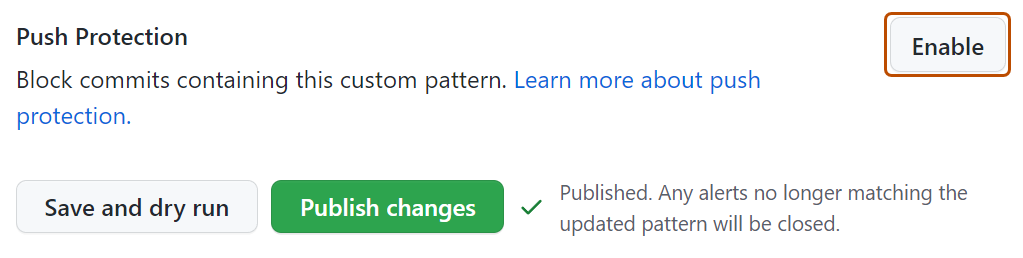
Optionally, to enable push protection for your custom pattern, click Enable.
Note
- Push protection for custom patterns will only apply to repositories that have secret scanning as push protection enabled. For more information about enabling push protection, see About push protection.
- Enabling push protection for commonly found custom patterns can be disruptive to contributors.
-
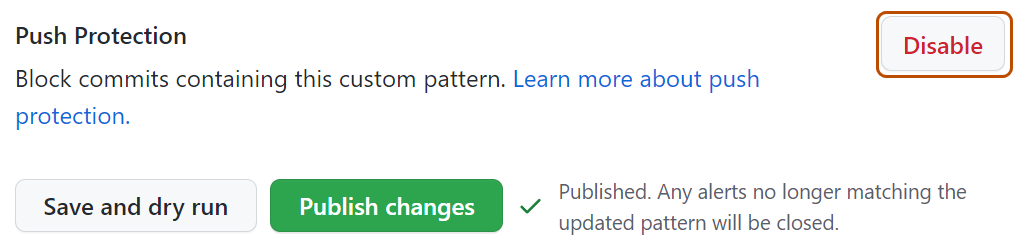
Optionally, to disable push protection for your custom pattern, click Disable.
Removing a custom pattern
When you remove a custom pattern, GitHub gives you the option to close the secret scanning alerts relating to the pattern, or keep these alerts.
- Navigate to where the custom pattern was created. A custom pattern can be created in a repository, organization, or enterprise account.
- For a repository or organization, display the "Security & analysis" settings for the repository or organization where the custom pattern was created. For more information, see Defining a custom pattern for a repository or Defining a custom pattern for an organization.
- For an enterprise, under "Policies" display the "Advanced Security" area, and then click Security features. For more information, see Defining a custom pattern for an enterprise account.
- To the right of the custom pattern you want to remove, click .
- Review the confirmation, and select a method for dealing with any open alerts relating to the custom pattern.
- Click Yes, delete this pattern.
Enabling push protection for a custom pattern
You can enable secret scanning as a push protection for custom patterns stored at the enterprise, organization, or repository level.
Enabling push protection for a custom pattern stored in an enterprise
Note
- To enable push protection for custom patterns, secret scanning as push protection needs to be enabled at the enterprise level. For more information, see About push protection.
- Enabling push protection for commonly found custom patterns can be disruptive to contributors.
Before enabling push protection for a custom pattern at enterprise level, you must also test your custom patterns using dry runs. You can only perform a dry run on repositories that you have administration access to. If an enterprise owner wants access to perform dry runs on any repository in an organization, they must be assigned the organization owner role. For more information, see Managing your role in an organization owned by your enterprise.
-
In the top-right corner of GitHub, click your profile photo.
-
Depending on your environment, click Your enterprise, or click Your enterprises then click the enterprise you want to view.
-
On the left side of the page, in the enterprise account sidebar, click Policies.
-
Under "Policies", click Code security.
-
Under "Code security", click Security features.
-
Under "Secret scanning", under "Custom patterns", click for the pattern of interest.
Note
At the enterprise level, you can only edit and enable push protection for custom patterns that you created.
-
To enable push protection for your custom pattern, scroll down to "Push Protection", and click Enable.
Note
The option to enable push protection is visible for published patterns only.

Enabling secret scanning as a push protection in an organization for a custom pattern
Before enabling push protection for a custom pattern at organization level, you must ensure that you enable secret scanning for the repositories that you want to scan in your organization. To enable secret scanning on all repositories in your organization, see Managing security and analysis settings for your organization.
-
In the upper-right corner of GitHub, select your profile photo, then click Your organizations.
-
Next to the organization, click Settings.
-
In the "Security" section of the sidebar, select the Code security dropdown menu, then click Global settings.
-
Under "Custom patterns", click for the pattern of interest.
-
To enable push protection for your custom pattern, scroll down to "Push Protection", and click Enable.
Note
- The option to enable push protection is visible for published patterns only.
- Push protection for custom patterns will only apply to repositories in your organization that have secret scanning as push protection enabled. For more information, see About push protection.
- Enabling push protection for commonly found custom patterns can be disruptive to contributors.

Enabling secret scanning as a push protection in a repository for a custom pattern
Before enabling push protection for a custom pattern at repository level, you must define the custom pattern for the repository, and test it in the repository. For more information, see Defining custom patterns for secret scanning.
-
On GitHub, navigate to the main page of the repository.
-
Under your repository name, click Settings. If you cannot see the "Settings" tab, select the dropdown menu, then click Settings.
-
In the "Security" section of the sidebar, click Code security.
-
Under "Code security", find "GitHub Advanced Security."
-
Under "Secret scanning", under "Custom patterns", click for the pattern of interest.
-
To enable push protection for your custom pattern, scroll down to "Push Protection", and click Enable.
Note
The option to enable push protection is visible for published patterns only.
