About dependency review enforcement
Enterprise owners and people with admin access to a repository can add the dependency review action to their enterprise and repository, respectively.
The "dependency review action" refers to the specific action that can report on differences in a pull request within the GitHub Actions context. See dependency-review-action. You can use the dependency review action in your repository to enforce dependency reviews on your pull requests. The action scans for vulnerable versions of dependencies introduced by package version changes in pull requests, and warns you about the associated security vulnerabilities. This gives you better visibility of what's changing in a pull request, and helps prevent vulnerabilities being added to your repository. For more information, see About dependency review.
You can enforce the use of the dependency review action in your organization by setting up a repository ruleset that will require the dependency-review-action workflow to pass before pull requests can be merged. Repository rulesets are rule settings that allow you to control how users can interact with selected branches and tags in your repositories. For more information, see About rulesets and Require workflows to pass before merging.
Prerequisites
You need to add the dependency review action to one of the repositories in your organization, and configure the action. For more information, see Configuring the dependency review action.
Enforcing dependency review for your organization
-
In the upper-right corner of GitHub, select your profile photo, then click Your organizations**.
-
Next to the organization, click Settings.
-
In the left sidebar, in the "Code, planning, and automation" section, click Repository, then click Rulesets.
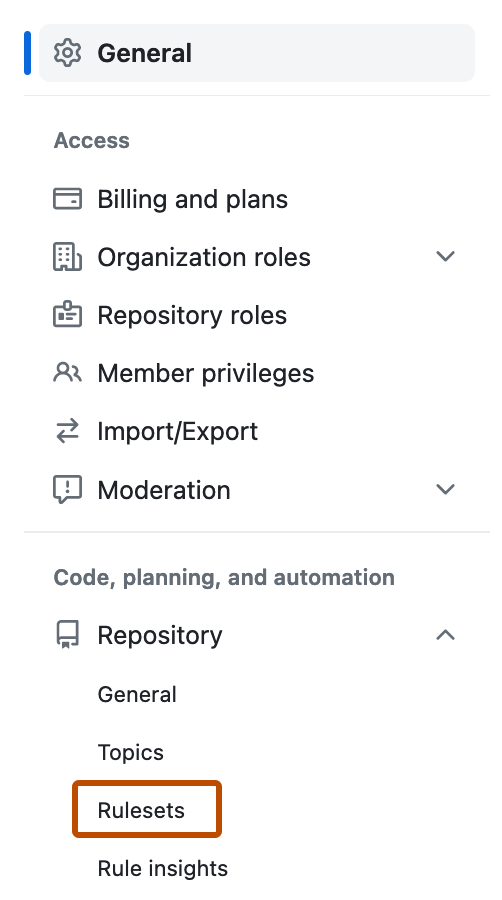
-
Click New branch ruleset.
-
Set Enforcement status to Active.
-
Optionally, you can target specific repositories in your organization. For more information, see Choosing which repositories to target in your organization.
-
In the "Rules" section, select the "Require workflows to pass before merging" option.
-
In "Workflow configurations", click Add workflow.
-
In the dialog, select the repository that you added the dependency review action to. For more information, see Prerequisites.
-
Select a branch and the workflow file for dependency review in the enhanced dialog.
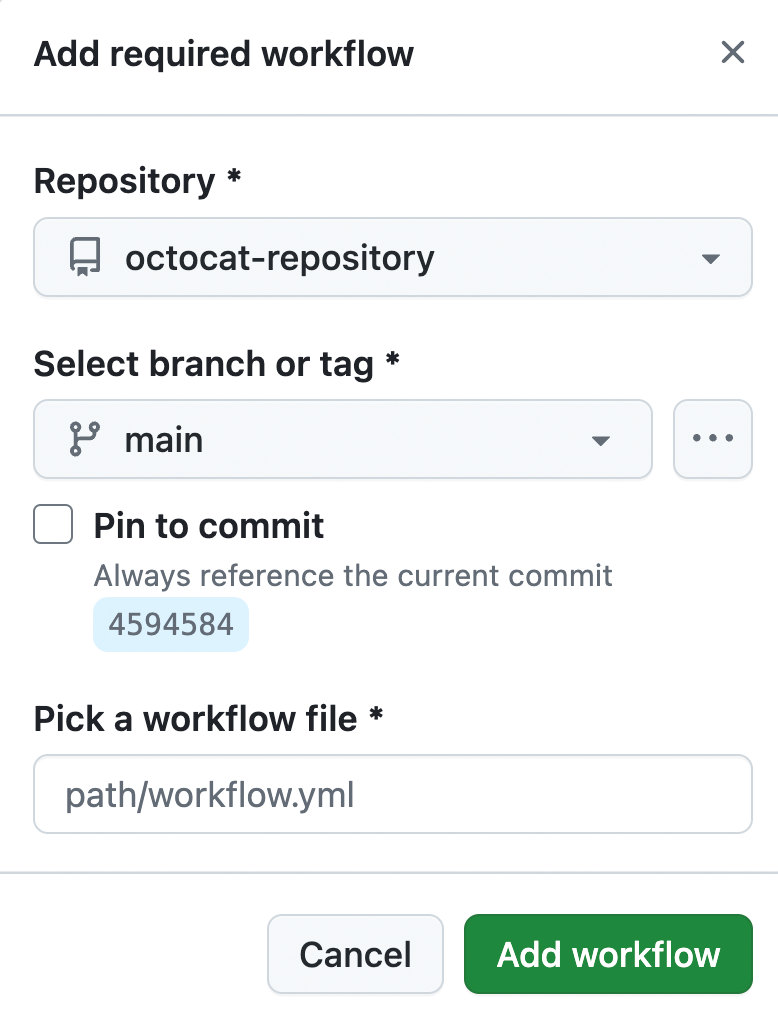
-
Click Create.