О внешнем хранилище для GitHub Actions
GitHub Actions использует внешнее хранилище BLOB-объектов для хранения данных, созданных рабочими процессами. Сохраненные данные включают журналы рабочих процессов, кэши и артефакты сборки, отправленные пользователем. Дополнительные сведения см. в разделе Начало работы с GitHub Actions для сервера GitHub Enterprise.
Существует два варианта настройки GitHub Enterprise Server для подключения к внешнему поставщику хранилища:
- OpenID Connect (OIDC)
- Традиционная проверка подлинности на основе учетных данных с помощью секретов
Мы рекомендуем использовать OIDC, если это возможно, так как вам не потребуется создавать конфиденциальные и длительные секреты учетных данных для поставщика хранилища и риск их предоставления. После определения доверия с помощью OIDC поставщик облачных хранилищ автоматически выдает маркеры доступа с коротким сроком действия к экземпляр GitHub Enterprise Server, которые автоматически истекают.
Необходимые компоненты
Перед включением GitHub Actions выполните следующие действия:
-
Создайте учетную запись хранения в Azure для хранения данных рабочего процесса. GitHub Actions хранит данные в виде блочных BLOB-объектов. Поддерживаются два типа учетных записей хранения:
-
Учетная запись хранения общего назначения (также известная как
general-purpose v1илиgeneral-purpose v2) с использованием стандартного уровня производительности.Warning
Использование уровня производительности premium с учетной записью хранения общего назначения не поддерживается. Стандартный уровень производительности должен быть выбран при создании учетной записи хранения, и его нельзя изменить позже.
-
Учетная запись хранения BlockBlobStorage, которая использует уровень производительности премиум.
Дополнительные сведения о типах учетных записей хранения в Azure и уровнях производительности см. в документации по Azure.
-
-
Ознакомьтесь с требованиями к оборудованию для GitHub Actions. Дополнительные сведения см. в разделе Начало работы с GitHub Actions для сервера GitHub Enterprise.
-
Протокол TLS должен быть настроен для домена GitHub Enterprise Server. Дополнительные сведения см. в разделе Настройка TLS.
Note
Настоятельно рекомендуется настроить TLS в GitHub Enterprise Server с сертификатом, подписанным доверенным центром авторизации. Хотя самозаверяющий сертификат можно использовать, необходимо дополнительно настроить локальные средства выполнения тестов, и не рекомендуется использовать сертификат для рабочих сред.
-
Если у вас есть http-прокси-сервер **, настроенный **на GitHub:
-
Необходимо добавить
.localhostи127.0.0.1``::1в список исключений **** прокси-сервера HTTP (в этом порядке). -
Если расположение внешнего хранилища не является маршрутизируемым, необходимо также добавить URL-адрес внешнего хранилища в список исключений.
Дополнительные сведения об изменении параметров прокси-сервера см. в разделе Настройка сервера веб-прокси исходящего трафика.
-
Если вы используете OIDC для подключения к поставщику хранилища, необходимо предоставить следующие URL-адреса службы маркеров OIDC на экземпляр GitHub Enterprise Server в общедоступном Интернете:
https://HOSTNAME/_services/token/.well-known/openid-configuration https://HOSTNAME/_services/token/.well-known/jwksЭто гарантирует, что поставщик хранилища может связаться с экземпляр GitHub Enterprise Server для проверки подлинности.
Включение GitHub Actions с хранилищем BLOB-объектов Azure с помощью OIDC (рекомендуется)
Чтобы настроить GitHub Enterprise Server для использования OIDC с учетной записью хранения Azure, необходимо сначала зарегистрировать приложение Microsoft Entra ID (ранее известное как Azure AD) с учетными данными OIDC, а затем настроить учетную запись хранения и, наконец, настроить GitHub Enterprise Server для доступа к контейнеру хранения с помощью идентификатора записи.
1. Регистрация приложения идентификатора записи
-
Войдите в Центр администрирования Microsoft Entra.
-
Зарегистрируйте новое приложение в идентификаторе Entra. Дополнительные сведения см. в кратком руководстве. Регистрация приложения с помощью платформа удостоверений Майкрософт в Microsoft Learn.
-
В приложении Идентификатора записи в разделе "Essentials" запишите значения для идентификатора приложения (клиента) и "Идентификатор каталога (клиента"). Эти значения используются позже.
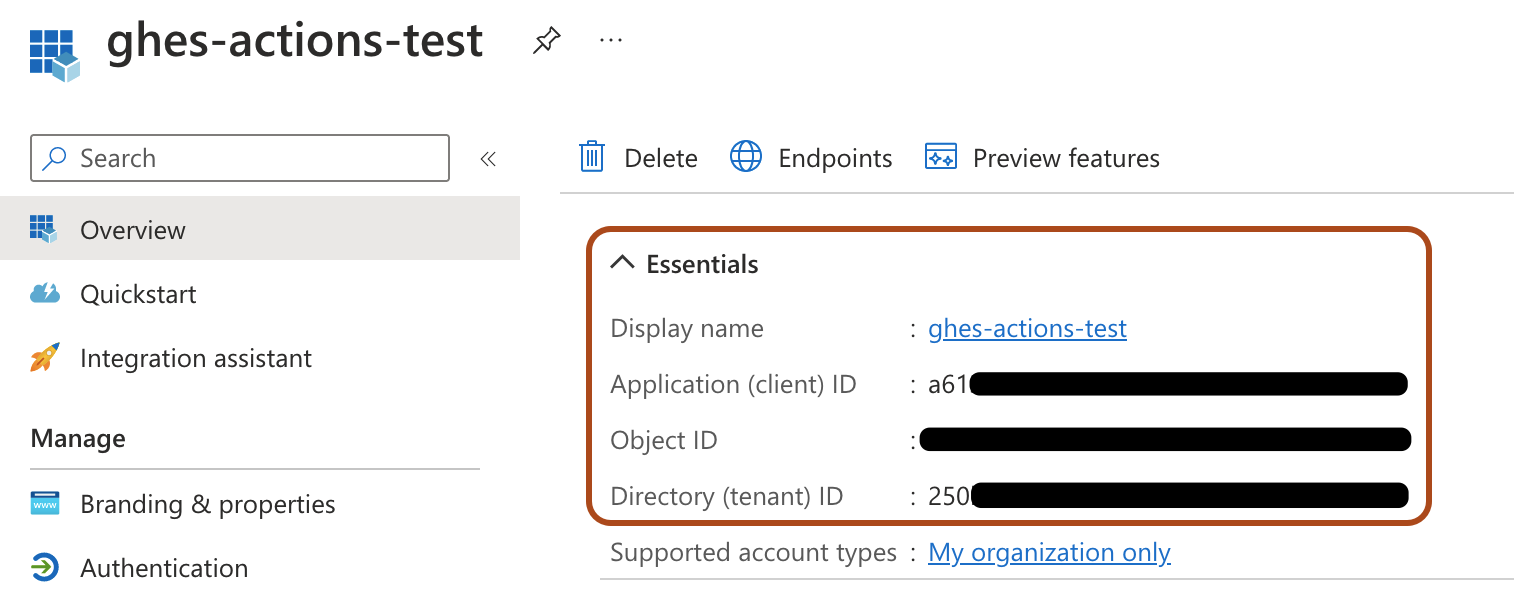
-
В приложении идентификатора записи в разделе "Управление" выберите вкладку "Сертификаты и секреты", перейдите на вкладку "Федеративные учетные данные", а затем нажмите кнопку "Добавить учетные данные".
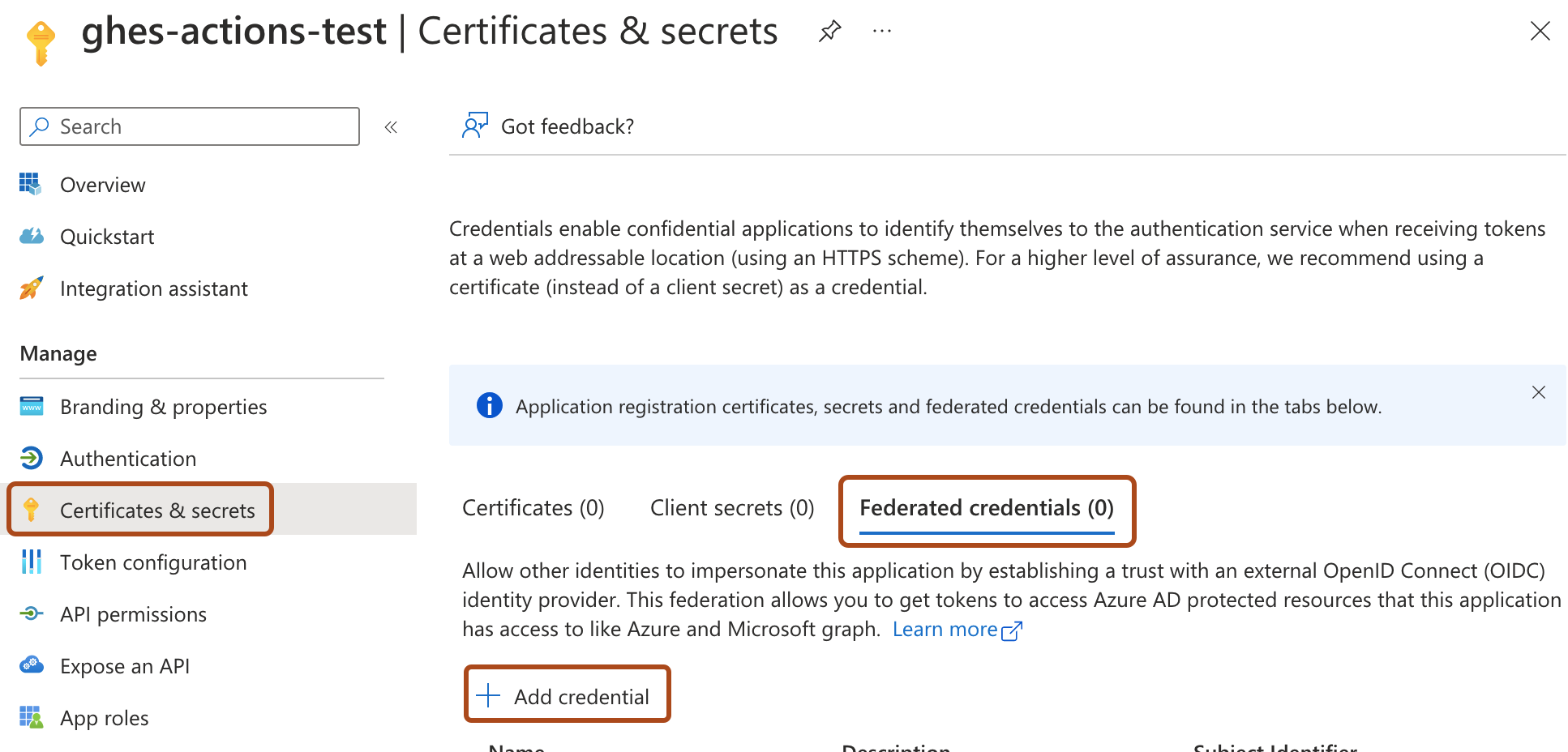
-
Введите следующие сведения для учетных данных:
-
В разделе "Сценарий федеративных учетных данных" выберите другой издатель.
-
В поле "Издатель" введите
https://HOSTNAME/_services/token``HOSTNAMEимя общедоступного узла для экземпляр GitHub Enterprise Server. Например,https://my-ghes-host.example.com/_services/token. -
В поле "Идентификатор субъекта" введите имя общедоступного узла для экземпляр GitHub Enterprise Server. Например,
my-ghes-host.example.com.Note
Идентификатор субъекта должен иметь только имя узла экземпляр GitHub Enterprise Server, и не должно включать протокол.
-
В поле "Имя" введите имя для учетных данных.
-
Нажмите кнопку Добавить.
-
2. Настройка учетной записи хранения
-
В microsoft портал Azure перейдите к учетной записи хранения.
-
Щелкните контроль доступа (IAM), а затем нажмите кнопку "Добавить" и выберите "Добавить назначение ролей".
-
Для роли выберите "Владелец данных BLOB-объектов хранилища", а затем нажмите кнопку "Далее".
-
Для участников щелкните "Выбрать участников **", а затем найдите **и выберите имя созданного ранее приложения Идентификатора записи. Щелкните Выбрать.
-
Нажмите кнопку "Рецензирование" и " Назначить", просмотрите назначение ролей, а затем нажмите кнопку "Проверить и назначить еще раз".
-
В меню слева в разделе "Параметры" щелкните "Конечные точки".
-
В разделе "Служба BLOB-объектов" запишите значение для службы BLOB-объектов, в частности суффикс конечной точки BLOB-объектов. Это значение после
https://<storageaccountname>.blob. Обычноcore.windows.netэто значение, но может отличаться в зависимости от вашего региона или типа учетной записи Azure.Например, если URL-адрес службы BLOB-объектов имеет значение, суффикс
https://my-storage-account.blob.core.windows.net``core.windows.netконечной точки BLOB-объектов.Обратите внимание на имя учетной записи хранения и суффикс конечной точки BLOB-объектов, так как эти значения используются позже.
3. Настройка GitHub Enterprise Server для подключения к идентификатору записи с помощью OIDC
-
В учетной записи администратора GitHub Enterprise Server, в правом верхнем углу любой страницы щелкните .
-
Если вы еще не на странице "Администратор сайта", в левом верхнем углу щелкните Администратор сайта.
-
На боковой панели " "Администратор сайта" щелкните Консоль управления.
-
На боковой панели "Параметры" нажмите кнопку "Действия".
-
В разделе "GitHub Actions" выберите "Включить действия GitHub".
-
В разделе "Артефакт и хранилище журналов" рядом с пунктом "Хранилище BLOB-объектов Azure" нажмите кнопку "Настройка".
-
В разделе "Проверка подлинности" выберите OpenID Connect (OIDC) и введите значения для хранилища, которое вы указали в предыдущих процедурах:
- Идентификатор клиента entra ID
- Идентификатор клиента entra ID
- Имя учетной записи хранения Azure
- Суффикс конечной точки BLOB-объектов Azure 1. Нажмите кнопку "Проверить параметры хранилища"**, **чтобы проверить параметры хранилища.
Если есть ошибки, проверяющие параметры хранилища, проверка параметры с поставщиком хранилища и повторите попытку.
-
На боковой панели "Параметры" нажмите кнопку "Сохранить параметры".
Note
Сохранение параметров в Консоль управления перезапускает системные службы, что может привести к простоям, видимым пользователем.
-
Подождите завершения запуска конфигурации.
Включение GitHub Actions с хранилищем BLOB-объектов Azure с помощью строка подключения
-
В учетной записи администратора GitHub Enterprise Server, в правом верхнем углу любой страницы щелкните .
-
Если вы еще не на странице "Администратор сайта", в левом верхнем углу щелкните Администратор сайта.
-
На боковой панели " "Администратор сайта" щелкните Консоль управления.
-
На боковой панели "Параметры" нажмите кнопку "Действия".
-
В разделе "GitHub Actions" выберите "Включить действия GitHub".
-
В разделе "Артефакт и хранилище журналов" рядом с пунктом "Хранилище BLOB-объектов Azure" нажмите кнопку "Настройка".
-
В разделе "Проверка подлинности" выберите "Учетные данные" и введите строка подключения учетной записи хранения Azure. Дополнительные сведения о получении строки подключения для учетной записи хранения см. в документации по Azure.
-
Нажмите кнопку "Проверить параметры хранилища"**, **чтобы проверить параметры хранилища.
Если есть ошибки, проверяющие параметры хранилища, проверка параметры с поставщиком хранилища и повторите попытку.
-
На боковой панели "Параметры" нажмите кнопку "Сохранить параметры".
Note
Сохранение параметров в Консоль управления перезапускает системные службы, что может привести к простоям, видимым пользователем.
-
Подождите завершения запуска конфигурации.
Следующие шаги
После успешного завершения выполнения конфигурации GitHub Actions будет включен на GitHub. Для следующих действий, таких как управление разрешениями доступа GitHub Actions и добавление локальных средств выполнения, вернитесь в Начало работы с GitHub Actions для сервера GitHub Enterprise.