Note: Your site administrator must enable secret scanning for your GitHub Enterprise Server instance before you can use this feature. For more information, see "Configuring secret scanning for your appliance."
You may not be able to enable or disable secret scanning, if an enterprise owner has set a policy at the enterprise level. For more information, see "Enforcing policies for code security and analysis for your enterprise."
About push protection for repositories and organizations
So far, secret scanning checks for secrets after a push and alerts users to exposed secrets. When you enable push protection for your organization or repository, secret scanning also checks pushes for supported secrets. Secret scanning lists any secrets it detects so the author can review the secrets and remove them or, if needed, allow those secrets to be pushed. Secret scanning can also check pushes for custom patterns. For more information, see "Defining custom patterns for secret scanning."
If a contributor bypasses a push protection block for a secret, GitHub:
- Creates an alert in the Security tab of the repository.
- Adds the bypass event to the audit log.
- Sends an email alert to organization or personal account owners, security managers, and repository administrators who are watching the repository, with a link to the secret and the reason why it was allowed.
This table shows the behavior of alerts for each way a user can bypass a push protection block.
| Bypass reason | Alert behavior |
|---|---|
| It's used in tests | GitHub creates a closed alert, resolved as "used in tests" |
| It's a false positive | GitHub creates a closed alert, resolved as "false positive" |
| I'll fix it later | GitHub creates an open alert |
You can monitor security alerts to discover when users are bypassing push protections and creating alerts. For more information, see "Auditing security alerts."
For information on the secrets and service providers supported for push protection, see "Secret scanning patterns."
Enabling secret scanning as a push protection
For you to use secret scanning as a push protection in public repositories, the enterprise, organization, or repository needs to have secret scanning enabled. For more information, see "Managing GitHub Advanced Security features for your enterprise," "Managing security and analysis settings for your organization," "Managing security and analysis settings for your repository," and "About GitHub Advanced Security."
Organization owners, security managers, and repository administrators can also enable push protection for secret scanning via the API. For more information, see "REST API endpoints for repositories" and expand the "Properties of the security_and_analysis object" section.
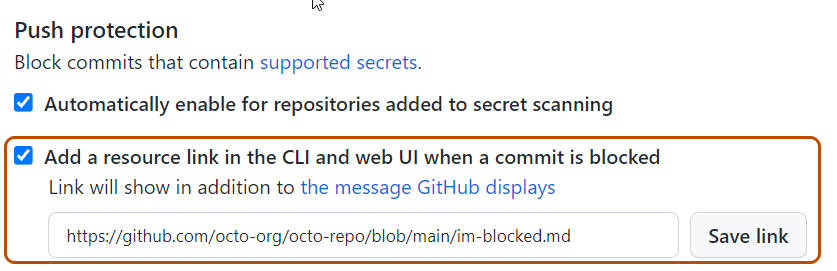
Organization owners can provide a custom link that will be displayed when a push is blocked. This custom link can contain organization-specific resources and advice, such as directions on using a recommended secrets vault or who to contact for questions relating to the blocked secret.
Enterprise administrators can also enable or disable secret scanning as a push protection for the enterprise via the API. For more information, see "REST API endpoints for enterprise code security and analysis."
Note: When you fork a repository with secret scanning as a push protection enabled, this is not enabled by default on the fork. You can enable it on the fork the same way you enable it on a standalone repository.
Enabling secret scanning as a push protection for your enterprise
-
In the top-right corner of GitHub Enterprise Server, click your profile photo, then click Enterprise settings.

-
On the left side of the page, in the enterprise account sidebar, click Settings.
-
In the left sidebar, click Code security and analysis.
-
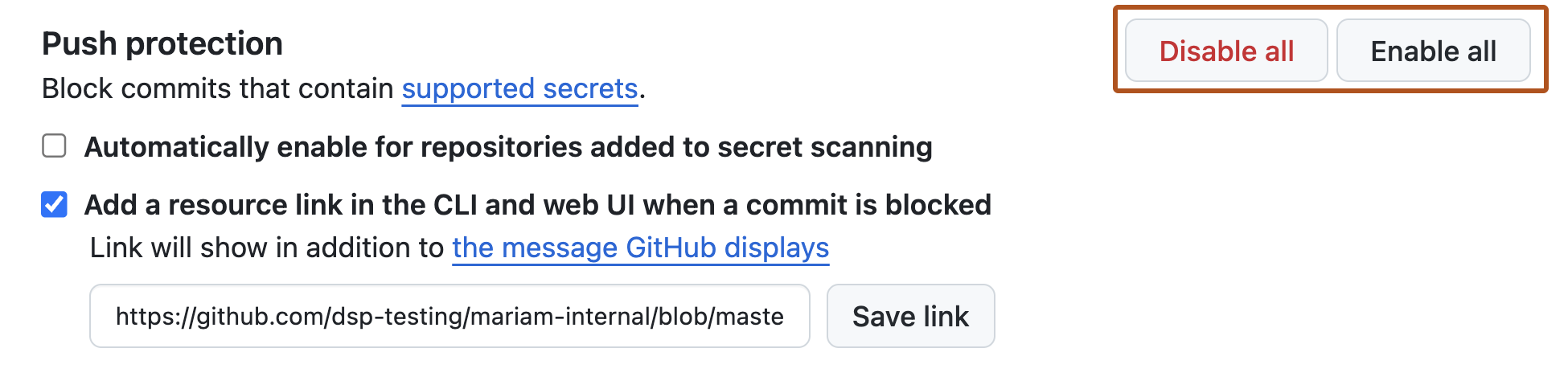
Under "Secret scanning", under "Push protection", click Enable all.
-
Optionally, click Automatically enable for repositories added to secret scanning.
-
Optionally, to include a custom link in the message that members will see when they attempt to push a secret, click Add a resource link in the CLI and web UI when a commit is blocked, then type a URL, and click Save link.
Enabling secret scanning as a push protection for an organization
You can use the organization settings page for "Code security and analysis" to enable or disable secret scanning as a push protection for all existing repositories in an organization.
-
On your GitHub Enterprise Server instance, navigate to the main page of the organization.
-
Under your organization name, click Settings. If you cannot see the "Settings" tab, select the dropdown menu, then click Settings.
-
In the "Security" section of the sidebar, click Code security and analysis.
-
Under "Code security and analysis", find "GitHub Advanced Security."
-
Under "Secret scanning", under "Push protection", click Enable all.
-
Optionally, click Automatically enable for repositories added to secret scanning.
-
Optionally, to include a custom link in the message that members will see when they attempt to push a secret, select Add a resource link in the CLI and web UI when a commit is blocked, then type a URL, and click Save link.

For more information about enabling security features across an organization, see "Quickstart for securing your organization."
Enabling secret scanning as a push protection for a repository
-
On your GitHub Enterprise Server instance, navigate to the main page of the repository.
-
Under your repository name, click Settings. If you cannot see the "Settings" tab, select the dropdown menu, then click Settings.
-
In the "Security" section of the sidebar, click Code security and analysis.
-
Under "Code security and analysis", find "GitHub Advanced Security."
-
Under "Secret scanning", under "Push protection", click Enable.
Enabling push protection for a custom pattern
You can enable secret scanning as a push protection for custom patterns stored at the enterprise, organization, or repository level.
Enabling push protection for a custom pattern stored in an enterprise
Notes:
- To enable push protection for custom patterns, secret scanning as push protection needs to be enabled at the enterprise level. For more information, see "Push protection for repositories and organizations."
- Enabling push protection for commonly found custom patterns can be disruptive to contributors.
Before enabling push protection for a custom pattern at enterprise level, you must also test your custom patterns using dry runs. You can only perform a dry run on repositories that you have administration access to. If an enterprise owner wants access to perform dry runs on any repository in an organization, they must be assigned the organization owner role. For more information, see "Managing your role in an organization owned by your enterprise."
-
In the top-right corner of GitHub Enterprise Server, click your profile photo, then click Enterprise settings.

-
On the left side of the page, in the enterprise account sidebar, click Policies.
-
Under "Policies", click Code security and analysis.
-
Under "Code security and analysis", click Security features.
-
Under "Secret scanning", under "Custom patterns", click for the pattern of interest.
Note
At the enterprise level, you can only edit and enable push protection for custom patterns that you created.
-
To enable push protection for your custom pattern, scroll down to "Push Protection", and click Enable.
Note
The option to enable push protection is visible for published patterns only.
Enabling secret scanning as a push protection in an organization for a custom pattern
Before enabling push protection for a custom pattern at organization level, you must ensure that you enable secret scanning for the repositories that you want to scan in your organization. To enable secret scanning on all repositories in your organization, see "Managing security and analysis settings for your organization."
-
In the upper-right corner of GitHub, select your profile photo, then click Your organizations.
-
Next to the organization, click Settings.
-
In the "Security" section of the sidebar, click Code security and analysis.
-
Under "Code security and analysis", find "GitHub Advanced Security."
-
Under "Secret scanning", under "Custom patterns", click for the pattern of interest.
-
To enable push protection for your custom pattern, scroll down to "Push Protection", and click Enable.
Notes:
- The option to enable push protection is visible for published patterns only.
- Push protection for custom patterns will only apply to repositories in your organization that have secret scanning as push protection enabled. For more information, see "Push protection for repositories and organizations."
- Enabling push protection for commonly found custom patterns can be disruptive to contributors.

Enabling secret scanning as a push protection in a repository for a custom pattern
Before enabling push protection for a custom pattern at repository level, you must define the custom pattern for the repository, and test it in the repository. For more information, see "Defining custom patterns for secret scanning."
-
On your GitHub Enterprise Server instance, navigate to the main page of the repository.
-
Under your repository name, click Settings. If you cannot see the "Settings" tab, select the dropdown menu, then click Settings.

-
In the "Security" section of the sidebar, click Code security and analysis.
-
Under "Code security and analysis", find "GitHub Advanced Security."
-
Under "Secret scanning", under "Custom patterns", click for the pattern of interest.
-
To enable push protection for your custom pattern, scroll down to "Push Protection", and click Enable.
Note
The option to enable push protection is visible for published patterns only.
