About evaluating alerts
There are some additional features that can help you to evaluate alerts in order to better prioritize and manage them. You can:
- Check the validity of a secret, to see if the secret is still active. Applies to GitHub tokens only. For more information, see Checking a secret's validity.
- Review a token's metadata. Applies to GitHub tokens only. For example, to see when the token was last used. For more information, see Reviewing GitHub token metadata.
Checking a secret's validity
Validity checks help you prioritize alerts by telling you which secrets are active or inactive. An active secret is one that could still be exploited, so these alerts should be reviewed and remediated as a priority.
By default, GitHub checks the validity of GitHub tokens and displays the validation status of the token in the alert view.
Organizations using GitHub Enterprise Cloud with a license for GitHub Advanced Security can also enable validity checks for partner patterns. For more information, see Checking a secret's validity in the GitHub Enterprise Cloud documentation.
| Validity | Status | Result |
|---|---|---|
| Active secret | active | GitHub checked with this secret's provider and found that the secret is active |
| Possibly active secret | unknown | GitHub does not support validation checks for this token type yet |
| Possibly active secret | unknown | GitHub could not verify this secret |
| Secret inactive | inactive | You should make sure no unauthorized access has already occurred |
You can use the REST API to retrieve a list of the most recent validation status for each of your tokens. For more information, see REST API endpoints for secret scanning in the REST API documentation. You can also use webhooks to be notified of activity relating to a secret scanning alert. For more information, see the secret_scanning_alert event in Webhook events and payloads.
Reviewing GitHub token metadata
Note
Metadata for GitHub tokens is currently in public preview and subject to change.
In the view for an active GitHub token alert, you can review certain metadata about the token. This metadata may help you identify the token and decide what remediation steps to take.
Tokens, like personal access token and other credentials, are considered personal information. For more information about using GitHub tokens, see GitHub's Privacy Statement and Acceptable Use Policies.
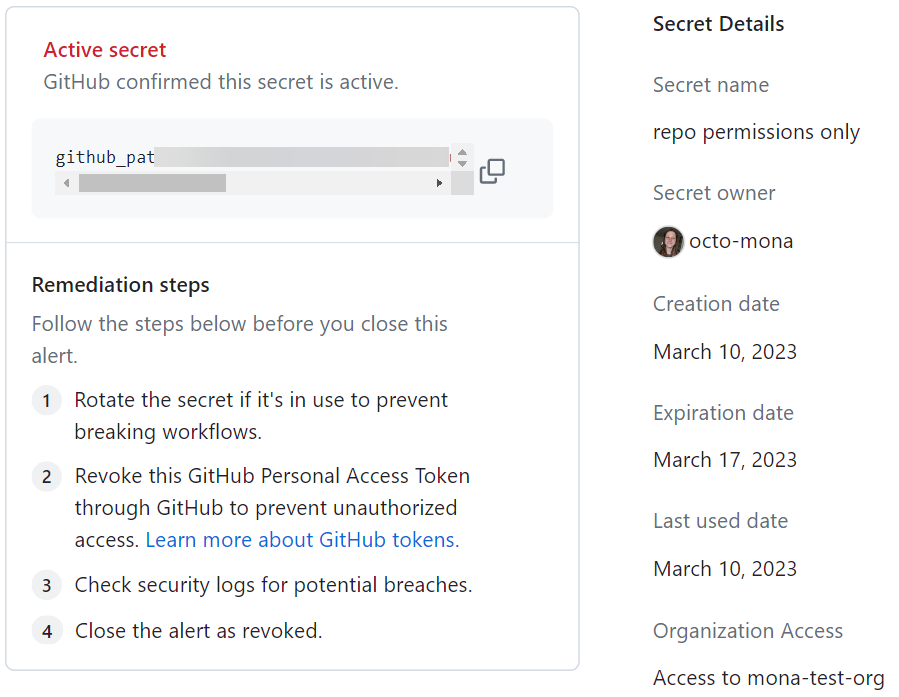
Metadata for GitHub tokens is available for active tokens in any repository with secret scanning enabled. If a token has been revoked or its status cannot be validated, metadata will not be available. GitHub auto-revokes GitHub tokens in public repositories, so metadata for GitHub tokens in public repositories is unlikely to be available. The following metadata is available for active GitHub tokens:
| Metadata | Description |
|---|---|
| Secret name | The name given to the GitHub token by its creator |
| Secret owner | The GitHub handle of the token's owner |
| Created on | Date the token was created |
| Expired on | Date the token expired |
| Last used on | Date the token was last used |
| Access | Whether the token has organization access |