You can secure your SSH keys and configure an authentication agent so that you won't have to re-enter your passphrase every time you use your SSH keys.
With SSH keys, if someone gains access to your computer, they also gain access to every system with which you use that key. To add an extra layer of security, you can add a passphrase to your SSH key. You can use ssh-agent to securely save your passphrase so you don't have to re-enter it.
Adding or changing a passphrase
You can change the passphrase for an existing private key without regenerating the keypair by typing the following command:
ssh-keygen -p # Start the SSH key creation process Enter file in which the key is (/Users/you/.ssh/id_rsa): [Hit enter] Key has comment '/Users/you/.ssh/id_rsa' Enter new passphrase (empty for no passphrase): [Type new passphrase] Enter same passphrase again: [One more time for luck] Your identification has been saved with the new passphrase.
If your key already has a passphrase, you will be prompted to enter it before you can change to a new passphrase.
Auto-launching ssh-agent on Git for Windows
Tip: If you're using the Git Shell that's installed with GitHub Desktop, you don't need to follow these steps. GitHub Desktop automatically launches the ssh-agent for you.
You can run ssh-agent automatically when you open bash or Git shell. Copy the following lines and paste them into your ~/.profile or ~/.bashrc file in Git shell:
env=~/.ssh/agent.env
agent_load_env () { test -f "$env" && . "$env" >| /dev/null ; }
agent_start () {
(umask 077; ssh-agent >| "$env")
. "$env" >| /dev/null ; }
agent_load_env
# agent_run_state: 0=agent running w/ key; 1=agent w/o key; 2= agent not running
agent_run_state=$(ssh-add -l >| /dev/null 2>&1; echo $?)
if [ ! "$SSH_AUTH_SOCK" ] || [ $agent_run_state = 2 ]; then
agent_start
ssh-add
elif [ "$SSH_AUTH_SOCK" ] && [ $agent_run_state = 1 ]; then
ssh-add
fi
unset env
Tip: If your private keys are not stored in ~/.ssh/id_rsa or ~/.ssh/id_dsa, you must add their paths with the ssh-add command so that your SSH authentication agent knows where to find them. For example:
ssh-add ~/.my_other_ssh/id_rsa
Now, when you first run Git Bash, you are prompted for your passphrase:
Initializing new SSH agent... succeeded Enter passphrase for /c/Users/you/.ssh/id_rsa: Identity added: /c/Users/you/.ssh/id_rsa (/c/Users/you/.ssh/id_rsa) Welcome to Git (version 1.6.0.2-preview20080923) > Run 'git help git' to display the help index. Run 'git help' to display help for specific commands.
The ssh-agent process will continue to run until you log out, shut down your computer, or kill the process.
If you want ssh-agent to forget your key after some time, you can configure it to do so by running ssh-add -t <seconds>.
OS X Keychain
If you are on OS X Leopard or later, ssh-agent runs automatically for you. It will also integrate with the keychain, so you can unlock your keys with it. This has some major advantages over a command-line based setup: for example, it protects your input from being copied or spied upon by universal access or low-level keyboard routines.
The default private key files (.ssh/id_rsa, .ssh/id_dsa, and .ssh/identity) should be handled automatically. If you have a private key with a different name, you can add it by typing ssh-add -K path/to/my_key.
Tip: Make sure you're using the default OS X ssh-add command, and not one installed by macports, homebrew, or some other external source.
When you first try to use the key, you are prompted to enter your passphrase:
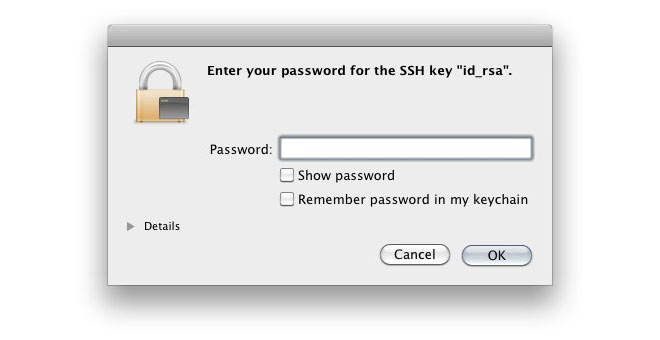
If you choose to save the passphrase with your keychain, you won't have to enter it again. Instead you'll simply need to unlock your keychain.