With 2FA enabled, you'll be asked to provide your 2FA authentication code, as well as your password, when you access GitHub Enterprise.
You'll be presented with a dialog asking you to enter your 2FA code, which will be generated from your TOTP application.
GitHub Enterprise will only ask you to provide your 2FA authentication code again if you've logged out, are using a new device, or your session expires.
If your authentication fails several times, you may wish to synchronize your phone's clock with your mobile provider. Often, this involves checking the "Set automatically" option on your phone's clock, rather than providing your own time zone.
Generating a code through a TOTP application
If you chose to set up two-factor authentication using a TOTP application on your smartphone, you can generate an authentication code for GitHub Enterprise at any time. After entering your username and password, you'll be asked for your "Two-factor authentication code". In most cases, just launching the application will generate a new code. You should refer to your application's documentation for specific instructions. You can then enter this code to gain access to your account.
If you delete the mobile application after configuring two-factor authentication, you'll need to provide your recovery code to get access to your account.
Using a FIDO U2F compatible security key
Note: FIDO U2F authentication is currently only available for the Chrome browser.
If you set up two-factor authentication via a security key, you can authenticate to GitHub Enterprise on your computer instead of using codes generated by a TOTP application . For specific instructions for authenticating with a security key, see the documentation for your device.
Authentication with a security key is secondary to authentication with a TOTP application. You'll still need to set up 2FA using a TOTP application before being able to enable a security key. If you lose your hardware key, you'll still be able to use your phone's code to sign in.
When you'll be asked for a 2FA code
After 2FA is enabled there are several scenarios where you'll be asked to provide your 2FA code:
Through the web
If you sign into GitHub Enterprise through the website, you'll be provided with the following prompt asking for your 2FA code:
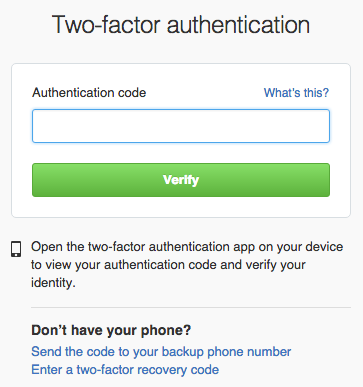
If you're providing a recovery code you previously downloaded from GitHub Enterprise, you will need to click the Enter a two-factor recovery code link and follow the instructions for entering your recovery code instead of entering it in the Authentication Code box.
Through the API
With 2FA enabled, you'll need to pass along a special header containing your 2FA authentication code. More information can be found within our Developer Documentation.
Through GitHub Desktop
After setting up 2FA and reauthenticating to GitHub Enterprise, you'll be provided with the following prompt asking for your 2FA code:
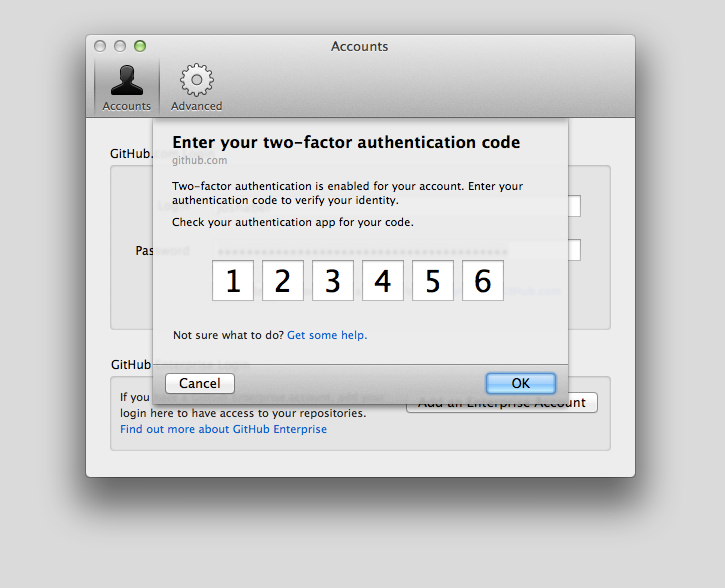
You'll be presented with a dialog asking you to enter your 2FA code, which will be generated from your TOTP application.
Through GitHub Desktop
After setting up 2FA and reauthenticating to GitHub Enterprise, you'll be provided with the following prompt asking for your 2FA code:
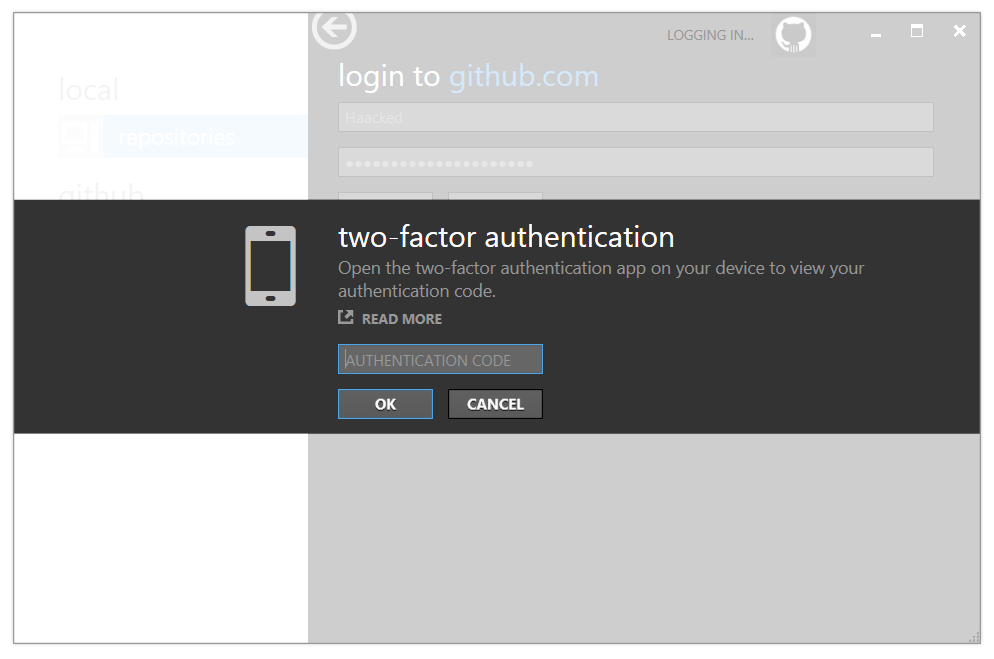
You'll be presented with a dialog asking you to enter your 2FA code, which will be generated from your TOTP application.
When you'll be asked for a personal access token as a password
After 2FA is enabled there are a couple of scenarios where you need to enter a personal access token instead of a 2FA code and your GitHub password.
Through the command line
You must create a personal access token to use as a password when authenticating to GitHub Enterprise on the command line using HTTPS URLs.
For example, when you access a repository using Git on the command line using commands like git clone, git fetch, git pull or git push with HTTPS URLs, you must provide your GitHub Enterprise username and your personal access token when prompted for a username and password. The command line prompt won't specify that you should enter your personal access token when it asks for your password.
2FA and Subversion (svn command line, tortoise svn, etc)
When you access a repository via Subversion, you must provide a personal access token instead of entering your password.
When you'll be asked for your SSH key passphrase as a password
If you have authenticated to GitHub Enterprise on the command line using SSH URLs you must enter an SSH key passphrase instead of a 2FA code and your GitHub password after 2FA is enabled.
For example, when you access a repository using Git on the command line using commands like git clone, git fetch, git pull or git push with SSH URLs, you must provide your SSH key passphrase when prompted for a password. The command line prompt won't specify that you should enter your SSH key passphrase when it asks for your password.